How to generate SSH key pairs
SSH keys are generated using the ssh-keygen program on Linux/Unix/ MacOS/Cygwin, or with PuTTYgen on Windows. For Windows users please go here
Please ensure that the 'Number of bits in a generated key' is 2048 or larger or your key will be rejected.
Linux/MacOS
- Open a terminal window on the desktop machine or laptop that you will be using to login to the RCF/ACF.
- At the prompt, type:
ssh-keygen -t rsa
You will see output similar to the following:Generating public/private rsa key pair. Enter file in which to save the key (/home/<user>/.ssh/id_rsa):
where<user>is replaced by your user name.
This command will generate an RSA key of the default length (2048 bits). - To accept the default file name and location
~/.ssh/id_rsa, press Return. - At the
Enter passphraseprompt, type in a pass phrase, which will not be echoed as you type, and then press Return.
This pass phrase will be used to unlock your private key file (failing to enter a pass phrase for your key will, of course, defeat all security related to the key pair). - You will be prompted to verify the pass phrase by entering it again. Retype your pass phrase, and then press Return.
The key pair will be generated, and you will see output similar to the following:Your identification has been saved in /home/<user>/.ssh/id_rsa. Your public key has been saved in /home/<user>/.ssh/id_rsa.pub. The key fingerprint is: SHA256:PFCKP1tBWnyxxXX+GM4g+ldsJ9/upHPNzloiQLX467c <user>@<machine.name>
... where the actual fingerprint for your key will be displayed (not the one shown in the example above), and where the terms in brackets (<>) are replaced by the values appropriate for your machine.
Two files will be created:- The first file is the private key, with the default name (or the name you entered above).
- The second file is the public key, with
.pubappended to the file name.
- Copy the key fingerprint value from the output above.
- To upload the key, browse to:
https://web.racf.bnl.gov/Facility/SshKeys/UploadSshKey.php
In order to view the form, you will be prompted for your Kerberos user name and password. - Click the Browse button, and in the dialog box, navigate to your
.sshdirectory (or the directory in which your public key file is stored).
If your browser does not display hidden directories (ones that begin with a period), then you will have to type in or cut and paste the name of the public key file into the dialog box. Enter the full name of the public key file (as displayed in output earlier), including the path and the.pubfile extension (if you copy and paste the name or path, take care to leave off the period at the end of the line with the public key file name). - Copy and paste the fingerprint of your public key (as displayed in output earlier) into the second box in the form, or type it into the dialog box. Starting with SHA256:
- To upload your key file, click the Send File button.
- You can now login to one of the gateway machines using SSH keys. You will be prompted for the passphrase for you private key during the login process. The passphrase will not leave your local machine.
Use an Existing Key Pair
- To obtain the fingerprint of an existing public key in your system's default format, use the command:
ssh-keygen -l -f [public_key_file_name]
where the first argument is a lower-case L, and<public key file name>is the full path to your public key file.
This command will return the default fingerprint hash of your public key, in output similar to the following:2048 SHA256:PFCKP1tBWnyxxXX+GM4g+IdsJ9/upHPNzloiQLX467c you@yourhost.com (RSA)
where your default fingerprint is prefixed by the text `SHA256:`.
Note: If you are using a version of OpenSSH older than v6.8, the default fingerprint is in MD5. - Proceed to upload your key as specified above.
The PuTTYgen program is used to generate a public/private key pair under Windows and will generate a 1024-bit RSA key by default. PuTTY programs are available from Simon Tatham.
Generate A New Key Pair using Putty for Windows users
- On the desktop machine or laptop that you will be using to login to the RACF, from the PuTTY submenu in the Start menu, open the PuTTYgen program.
- Using the defaults, click the Generate button, and then move your mouse around in the space above the Generate button.
Ensure that the 'Number of bits in a generated key' at the bottom of the GUI is 2048 or larger or your key will be rejected. - When the key pair generation has completed, you will see a result similar to the following image, with both the Save public key and Save private key buttons now active. If desired, you can change the value of the Key comment: field.
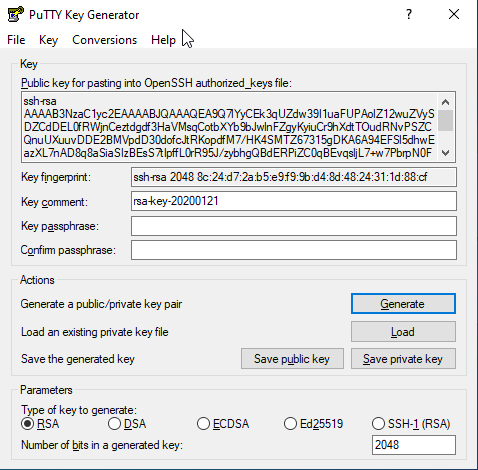
- Enter a Key passphrase and Confirm passphrase for password protection on the generated key.
- To save your new keys, click the Save public key and Save private key buttons.
The default save location for both files is the folder just above your My Documents folder, and your private key will have the file extension.ppk.
Keep this window open so that you can copy and paste the key fingerprint later in the procedure. - To upload your key file, browse to:
https://web.racf.bnl.gov/Facility/SshKeys/UploadSshKey.php
In order to view the form, you will be prompted for your Kerberos user name and password. - Click the Browse button, and in the dialog box, navigate to your
~/.sshdirectory (or the directory in which your public key file is stored).
The dialog box will likely open in the default location for the key files. If not, you will need to navigate to the appropriate folder. Once in the correct folder, select the public key file, and click Open. - Copy and paste your public key fingerprint from the Key fingerprint: field of the PuTTY Key Generator into the second box in the form, or type it manually into the dialog box. The key is comprised of 16 2-digit hexadecimal numbers separated by colons (
:). - To upload your key file, click the Send File button.
- You can now login to one of the gateway machines using SSH keys. You will be prompted for the passphrase for you private key during the login process. The passphrase will not leave your local machine.
Using an Existing Key Pair with Putty
- To load an existing key into the PuTTY Key Generator, and to obtain the fingerprint of an existing public key, click on the Load button.
- Proceed to upload your key as specified above.
Use an Existing Linux Key Pair on a Windows Machine
- If you have already uploaded a Linux public key to LDAP, you can use the same private key on your Windows machine by copying the Linux private key to your Windows machine, and converting the key to PuTTY format.
- After copying the private key to your Windows machine, launch the PuTTY Key Generator, and from the Conversions menu, choose Import.
- In the dialog box, browse to and select the private key file. As the file is imported, you will be prompted to enter its passphrase.
- After importing the key, to save it in .ppk format and use it on your Windows machine, click Save private key.
- It may be necessary to convert your public key as well: to do so, click Save public key.
Use an Existing Windows Key Pair on a Linux Machine
- To use a key that was generated in Windows on a Linux machine, from the PuTTY Key Generator's Conversions menu, choose Export OpenSSH Key, and then copy the resulting files into the
.sshdirectory of the Linux machine.
For More Information
For additional information on using SSH keys with PuTTY, see:
http://the.earth.li/~sgtatham/putty/0.60/htmldoc/Chapter8.html
