| Oracle Advanced Networking Option Administrator's Guide | Library |
Product |
Contents |
Index |
| Oracle Advanced Networking Option Administrator's Guide | Library |
Product |
Contents |
Index |
The name of the principal should have the following format:
Note: The utility names in this section are actual programs that you run. However, the Kerberos user name "krbuser" and realm "SOMECO.COM" are examples only--the actual names may vary among systems.
For example, if kservice is "oracle", and the fully-qualified name of the machine on which Oracle is running is "dbserver.someco.com", and if the realm is "SOMECO.COM", the principal name would be:
oracle/dbserver.someco.com@SOMECO.COM
Note: It is a common convention to use the DNS domain name as the name of the realm.
To create the service principal, run kdb5_edit as root:
# cd /krb5/admin
# ./kdb5_edit
To add a principal called "oracle/dbserver.someco.com@SOMECO.COM" to the list of server principals known by Kerberos, do the following:
kdb5_edit: ark oracle/dbserver.someco.com@SOMECO.COM
For example, to extract a service table for dbserver.someco.com, do the following:
kdb5_edit: xst dbserver.someco.com oracle
'oracle/dbserver.someco.com@SOMECO.COM' added to keytab 'WRFILE:dbserver.someco.com-new-srvtab'
kdb5_edit: exit
oklist -k -t dbserver.someco.com-new-srvtab
Note: After the service table has been extracted, verify that the new entries are in the table in addition to the old ones. If they are not, or you need to add more, use kdb5_edit to append the additional entries.
Note: If you do not enter a REALM (for example, SOMECO.COM) when using xst, it uses the realm of the current host and displays it in the command output, as shown above.
Note: If the Kerberos service table is on the same machine as the Kerberos client, you can simply move it. If the service table is on a different machine from the Kerberos client, you must transfer the file with a program like ftp.
# mv dbserver.someco.com-new-srvtab /etc/v5srvtab
Note: /etc/v5srvtab is the default name of the service file. If a different name is used, then that should be substituted for the default name.
Note: Do not make the file readable to all users. This may allow a security breach.
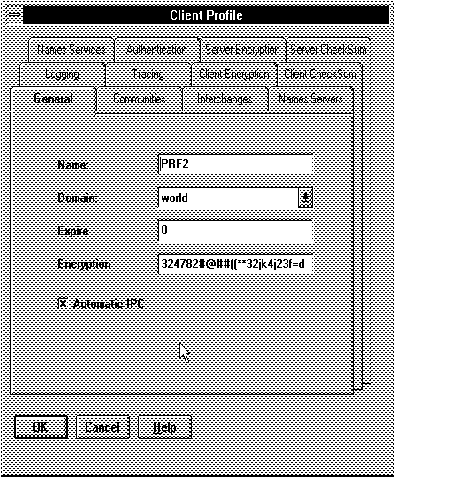 Figure 5 - 1. Client Profile: General Page
Figure 5 - 1. Client Profile: General Page
Note: Network Manager creates a Client Profile for every community created (for example, TCP.world), and for every node that is a member of more than one community. If you create additional Client Profiles, Network Manager names them PRF2, PRF3, and so forth. Change the names to something more meaningful.
Attention: You configure both clients and servers in your network by using the Client Profile pages.
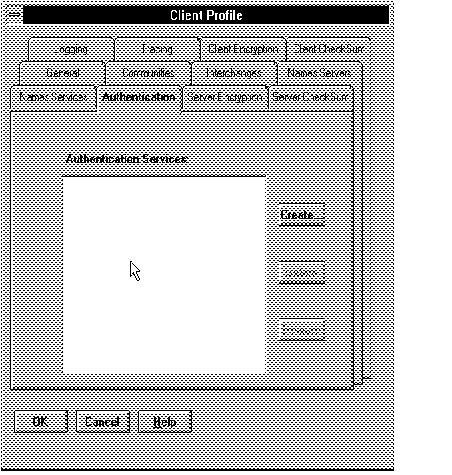 Figure 5 - 2. Client Profile: Initial Authentication Page
Figure 5 - 2. Client Profile: Initial Authentication Page
To configure the Oracle Kerberos authentication adapter, select Create from the Initial Authentication page. The Authentication Services page pops up, as shown in Figure 5 - 3.
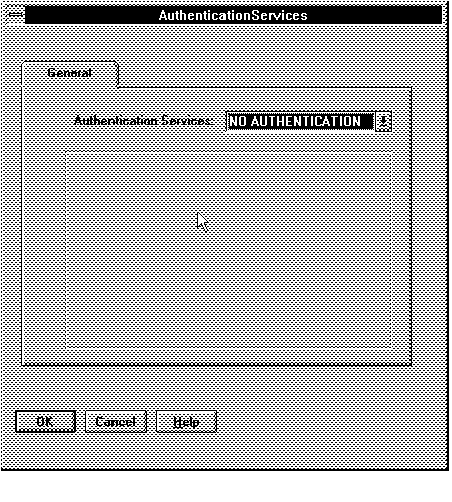 Figure 5 - 3. Default Authentication Services Page
Figure 5 - 3. Default Authentication Services Page
The default is NO AUTHENTICATION.
If you want to specify one or more authentication services to be used in a specific order, select one of the authentication services from the drop down list at the top of the page. Choices are: Access Manager, CyberSAFE, Identix, Kerberos (V5), NO AUTHENTICATION, and SecurID.
Note: Access Manager is not supported in this release of the Advanced Networking Option.
Attention: Do not select an authentication service unless it is installed and linked into your SQL*Net network. If you do, it will cause connections to fail because they will look for authentication where none is available.
Each authentication adapter you select has different parameters for which you may need to supply values. (Some parameters are required and some are optional.) The parameters appear in the middle of each authentication service's page. You will be prompted to enter all the required parameters for each authentication adapter.
For further information about how to use Oracle Network Manager to configure authentication services, see the Oracle Network Manager Administrator's Guide.
Note: Sample entries for the Kerberos parameters are shown in Figure 5 - 4. Only the Kerberos (V5) entry will actually display.
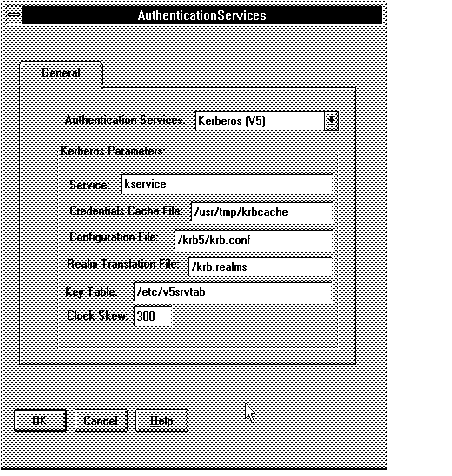 Figure 5 - 4. Kerberos Authentication Page
Figure 5 - 4. Kerberos Authentication Page
Service This required parameter specifies the name of the service Oracle will use to obtain a Kerberos service ticket. There is no default--you must define one.
Note: If you do not enter a value for Service, you will be prompted to enter one when you try to generate configuration files.
Credentials Cache File This optional parameter specifies the complete pathname to the Kerberos credentials cache file. The default value is operating system-dependent. For UNIX, it is /tmp/krb5cc_uid.
Configuration File This optional parameter specifies the complete pathname to the Kerberos configuration file. The configuration file contains the realm for the default KDC (key distribution center) and maps the realms to KDC hosts. The default on UNIX is /krb5/krb.conf.
Realm Translation File The optional parameter specifies the complete pathname to the Kerberos realm translation file. The translation file provides mapping from a host name or domain name to a realm. The default is operating-system dependent. For example, on UNIX, it is /krb5/krb.realms.
Key Table This optional parameter specifies the complete pathname to the Kerberos principal/secret key mapping file. It is used by the Oracle server to extract its key and decrypt the incoming authentication information from the client. The default is operating system-dependent. For UNIX, it is /etc/v5srvtab.
Network Delay This optional parameter specifies how many seconds can pass before a Kerberos credential is considered out-of-date. It is used when a credential is actually received by either a client or a server. It is also used by an Oracle server to decide if a credential needs to be stored to protect against a replay attack. The default is 300 seconds.
Note: Do these steps on the authentication server (where the administration tools are installed). It is assumed that the realm already exists. (Refer to the Kerberos documentation listed in the Preface if the realm needs to be created.)
Note: The utility names in this section are actual programs that you run. However, the Kerberos user name "krbruser" and realm "SOMECO.COM" are examples only; these may vary among systems.
# ./kdb5_edit
kdb5_edit: ank krbuser
Enter password: <password not echoed to screen>
Re-enter password for verification: <password...>
kdb5_edit: quit
Note: You should be on the Oracle server before performing the following commands:
SVRMGR> connect internal;
SVRMGR> create user "KRBUSER@SOMECO.COM"
identified externally;
SVRMGR> grant create session to
"KRBUSER@SOMECO.COM"; Note: In this example, OS_AUTHENT_PREFIX is set to "".
Attention: When creating the Oracle user, the name must be in upper-case and double-quoted; for example, "KRBUSER@SOMECO.COM".
sqlplus /@oracle
will follow a database link, you must use the forwardable flag (-f option). okinit -f enables credentials that can be used across database links.
Note: You should be on the Oracle client before running the following commands.
% okinit -f
Password for krbuser@SOMECO.COM:
<password not echoed to screen>
Note: You should be on the Oracle client before running these commands.
These utilities are intended for customers who are running an Oracle client with an Oracle Kerberos authentication adapter installed.
Note: Solaris is shipped with Kerberos version 4. Make sure that the Kerberos version 5 utilities are in your path so that the version 4 utilities are not inadvertently used.
Ask for a forwardable ticket-granting ticket. This option is necessary to follow database links.
-l
Specify the lifetime of the ticket-granting ticket and all subsequent tickets. By default, the ticket-granting ticket is good for eight (8) hours, but shorter or longer-lived credentials may be desired. Note that the key distribution center (KDC) can ignore this option or put site-configured limits on what can be specified. The lifetime value is a string that consists of a number qualified by 'w', 'd', 'h', 'm', or 's' meaning weeks, days, hours, minutes, or seconds, respectively. Example: okinit -l 2wld6h20m30s means ask for a ticket-granting ticket that has a lifetime of 2 weeks, 1 day, 6 hours, 20 minutes, and 30 seconds.
-c
Specify an alternative credential cache. For UNIX, the default is /tmp/krb5cc_<uid>. The alternate credential cache can also be specified by using the SQLNET.KERBEROS5_CC_NAME parameter in the SQLNET.ORA file.
-?
List command line options.
% oklist -f 27-Jul-1995 21:57:51 28-Jul-1995 05:58:14 krbtgt/SOMECO.COM@SOMECO.COM Flags: FI
Show flags with credentials. The important ones for Oracle are 'I' (credential is a ticket-granting ticket), 'F' (credential is forwardable), and 'f' (credential is forwarded).
-c
Specify an alternative credential cache. For UNIX, the default is /tmp/krb5cc_<uid>. The alternate credential cache can also be specified by using the SQLNET.KERBEROS5_CC_NAME parameter in the SQLNET.ORA file.
-k
List the entries in the service table (default /etc/v5srvtab) on UNIX. The alternate service table can also be specified by using the SQLNET.KERBEROS5_KEYTAB parameter in the SQLNET.ORA file.
% okdstry -f
Specify an alternative credential cache. For UNIX, the default is /tmp/krb5cc_<uid>. The alternate credential cache can also be specified by using the SQLNET.KRB5_CC_NAME parameter in the SQLNET.ORA file.
Attention: You should only manually configure files if you do not have access to Oracle Network Manager. See "Configuring the Kerberos authentication adapter with Oracle Network Manager".
sqlnet.authentication_services=(BEQ,KERBEROS5)
sqlnet.authentication_services=(BEQ,KERBEROS5)
sqlnet.authentication_kerberos5_service=kservice
Note: The second parameter specifies the name of the service Oracle will use to obtain a Kerberos service ticket. You must substitute a value for the kservice part of the service name.
Example: sqlnet.authentication_kerberos5_service=oracle
REMOTE_OS_AUTHENT=FALSE
Attention: Setting REMOTE_OS_AUTHENT to TRUE may create a security hole because it allows someone using a non-secure protocol (for example, TCP) to perform an operating system-authorized login (formerly referred to as an OPS$ login).
Because Kerberos user names can be long and Oracle user names are limited to 30 characters, it is strongly recommended that the following null value be used for the value of OS_AUTHENT_PREFIX:
OS_AUTHENT_PREFIX=""
Setting OS_AUTHENT_PREFIX to a null value overrides the default value of OPS$.
After modifying the configuration files, restart the Oracle server so that the changes will take effect. (For information on how to restart the Oracle server refer to your operating system-specific documentation and to the Oracle7 Server Administrator's Guide.)
Optional SQLNET.ORA Parameters In addition to the above required parameters, you can optionally set the following five parameters described below on the client or server:
SQLNET.KERBEROS5_CC_NAME= <pathname_to_credentials_cache_file>
Example: sqlnet.kerberos5_cc_name=/usr/tmp/krbcache
Note: You can also set this parameter by using the KRB5CCNAME environment variable. The value set for the SQLNET.KERBEROS5_CC_NAME parameter in the SQLNET.ORA file takes precedence over the value set in the KRB5CCNAME environment variable.
SQLNET.KERBEROS5_CLOCKSKEW= number_of_seconds_accepted_as_network_delay
Example: sqlnet.kerberos5_clockskew=1200
SQLNET.KERBEROS5_CONF= pathname_to_Kerberos_configuration_file
Example: sqlnet.kerberos5_conf=/krb5/krb.conf
SQLNET.KERBEROS5_KEYTAB= pathname_to_Kerberos_principal/key_table
Example: sqlnet.kerberos5_keytab=/etc/v5srvtab
SQLNET.KERBEROS5_REALMS= pathname_to_Kerberos_realm_translation_file
Example: sqlnet.kerberos5_realms=/krb5/krb.realms
If you cannot get your ticket-granting ticket using okinit:
|
Prev Next |
Copyright © 1996 Oracle Corporation. All Rights Reserved. |
Library |
Product |
Contents |
Index |